3 Tips For Choosing The Best Access Control
Tips for Hiring the Right Car Parking Access Control Systems
Selective constraint of access to a place or other resource, allowing only authorized users A sailor checks an identification card (ID) prior to permitting a vehicle to go into a military installation.
Physical gain access to control is a matter of who, where, and when. An access control system determines who is allowed to go into or leave, where they are allowed to exit or enter, and when they are permitted to enter or exit.
A wide variety of credentials can be utilized to replace mechanical keys. The electronic access control system grants gain access to based on the credential provided. When gain access to is granted, the door is unlocked for a fixed time and the transaction is recorded. When access is refused, the door remains locked and the attempted gain access to is tape-recorded.
When a credential is provided to a reader, the reader sends out the credential's information, generally a number, to a control panel, an extremely reliable processor. The control board compares the credential's number to a gain access to control list, grants or denies the presented demand, and sends a deal log to a database.
How to find a good Face Recognition Access Control
The control panel also ignores a door open signal to avoid an alarm.
Qualifications can be passed around, therefore subverting the gain access to control list. Alice has gain access to rights to the server room, but Bob does not. Alice either provides Bob her credential, or Bob takes it; he now has access to the server space. To prevent this, two-factor authentication can be used.
This is a crucial safety function. In cases where the lock need to be electrically opened on exit, the request-to-exit device also unlocks the door. Access control topology [modify] Typical gain access to control door wiring Gain access to control door electrical wiring when using smart readers Gain access to control decisions are made by comparing the qualifications to an access control list.
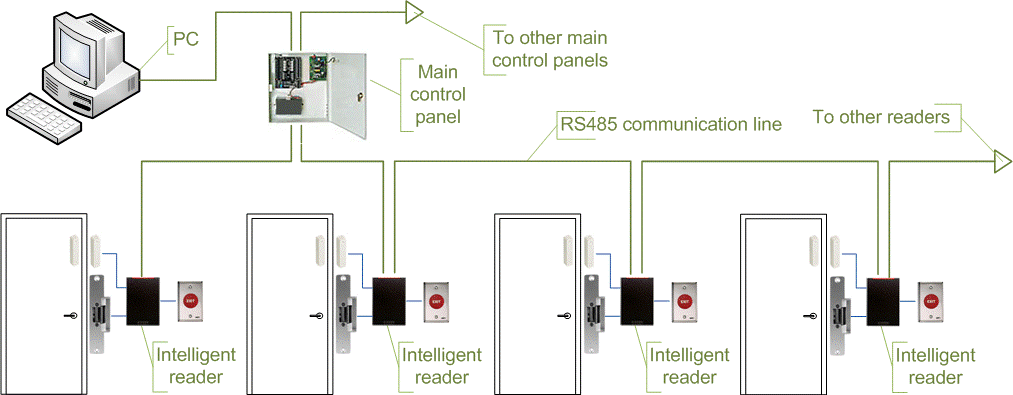
Normally, Wiegand procedure is used for transmitting information to the control board, however other alternatives such as RS-232, RS-485 and Clock/Data are not unusual. This is the most popular type of gain access to control readers. Examples of such readers are RF Tiny by RFLOGICS, Prox, Point by HID, and P300 by Farpointe Data.
Tips to Find the Best Parking Access Control Systems
When a user provides a card or enters a PIN, the reader sends info to the main controller, and waits on its response. If the connection to the main controller is disturbed, such readers stop working, or function in a degraded mode. Typically semi-intelligent readers are linked to a control panel by means of an RS-485 bus.
There is likewise a new generation of smart readers referred to as "IP readers". Systems with IP readers generally do not have conventional control board, and readers communicate straight to a PC that serves as a host. Some readers might have extra functions such as an LCD and function buttons for data collection purposes (i.
RS-485 does not allow the host PC to interact with several controllers connected to the exact same port concurrently. In big systems, transfers of configuration, and users to controllers might take a very long time, interfering with typical operations. Controllers can not initiate communication in case of an alarm. The host PC functions as a master on the RS-485 communication line, and controllers have to wait up until they are polled.
Tips in Finding the Best Vehicle Access Control Systems

Separate RS-485 lines have actually to be installed, rather of using an already existing network facilities. Operation of the system is extremely reliant on the host PC.
Access Control by Fresh USA
9 Mc Gregor Ct, Hawthorn Woods, IL 60047+1 (312) 312-9608
Click here learn more about Access Control
The general expense of the system is lower, as sub-controllers are usually simple and low-cost gadgets. Operation of the system is extremely dependent on primary controllers. Access control systems using serial controllers and terminal servers 4.
Interaction with the controllers may be done at the complete network speed, which is crucial if transferring a lot of data (databases with countless users, potentially including biometric records). In case of an alarm, controllers may start connection to the host PC. This ability is essential in large systems, since it serves to lower network traffic triggered by unneeded polling.
Tips for finding a Good Vehicle Access Control Gates
In case the host PC stops working, occasions from controllers are not obtained and operates that need interaction between controllers (i. e. anti-passback) stop working. Some controllers, however, have a peer-to-peer interaction choice in order to lower reliance on the host PC - access control software.

Benefits: [] A lot of IP readers are Po, E capable. This function makes it extremely simple to supply battery backed power to the entire system, including the locks and various kinds of detectors (if used). IP readers get rid of the need for controller enclosures. There is no squandered capacity when utilizing IP readers (e.
a 4-door controller would have 25% of unused capability if it was managing only 3 doors). IP reader systems scale quickly: there is no requirement to set up brand-new primary or sub-controllers. Failure of one IP reader does not impact any other readers in the system. Downsides: [] In order to be used in high-security locations, IP readers require special input/output modules to get rid of the possibility of invasion by accessing lock and/or exit button wiring.
3 Tips For Choosing The Right Access Control Systems
Being more advanced than standard readers, IP readers are also more pricey and sensitive, for that reason they should not be set up outdoors in areas with extreme weather, or high likelihood of vandalism, unless particularly designed for exterior setup. A couple of manufacturers make such designs. The benefits and downsides of IP controllers apply to the IP readers.
Often the legitimate user will hold the door for the trespasser. This risk can be minimized through security awareness training of the user population or more active ways such as gates. In really high-security applications this risk is lessened by utilizing a sally port, sometimes called a security vestibule or mantrap, where operator intervention is needed probably to guarantee legitimate recognition.
This access control system looks fine
ReplyDelete